A Bit-Optimal, Provably Secure Encryption Scheme from any Trapdoor Permutation
Keywords:
Asymmetric encryption,, provable security,, one-way invertible function,, ciphertext indistinguishability,, idealized hash function paradigmAbstract
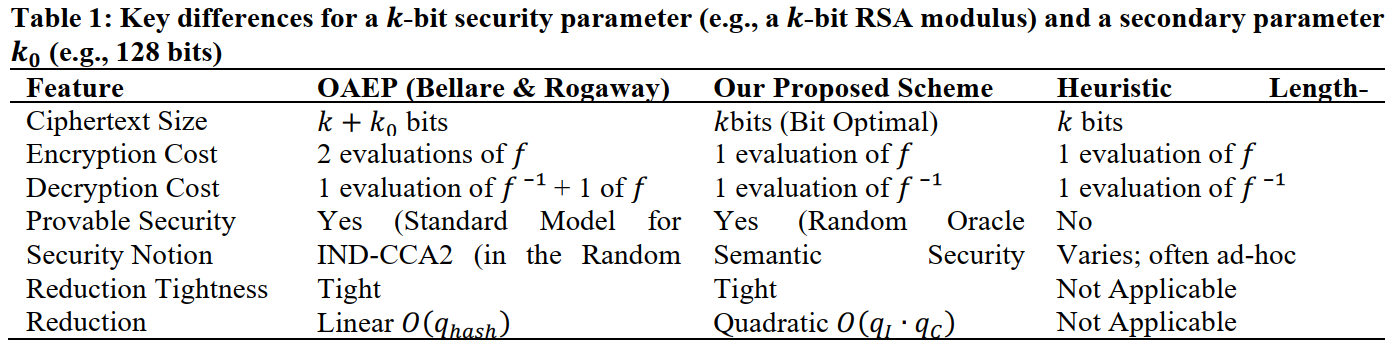
This study presents a provably secure asymmetric encryption scheme designed for optimal efficiency. A transmitter utilizes a -bit one-way invertible function to encode a message for a receptor holding the inverse . The construction ensures that encryption requires only a single computation of , decryption requires only a single computation of , the ciphertext length is exactly bits, and the permissible message length is nearly . The method employs a probabilistic encoding of into a string , with the ciphertext given by . Under the assumption of industry-standard compression function with any one-way invertible function, we describe and rigorously prove the security of this invertible enmesh scheme. The scheme is bit-optimal, allowing for the encryption of messages of length close to , and achieves semantic security—a strong notion that implies security against chosen-ciphertext attacks (CCA) and non-malleability in the standard-hash model.
Published
How to Cite
Issue
Section
How to Cite
Most read articles by the same author(s)
- Fatai Akangbe Hammed, Olumuyiwa Olawale Akanbi, Mustapha Adewale Usman, Sefiu Adekunle Onitilo, Ibrahim Adeyemi, Numerical Computation of Transient Magnetohydrodynamic Micropolar Fluid Flow through a Permeable Surface , Nigerian Journal of Physics: Vol. 34 No. 1 (2025): Nigerian Journal of Physics - Vol. 34 No. 1




